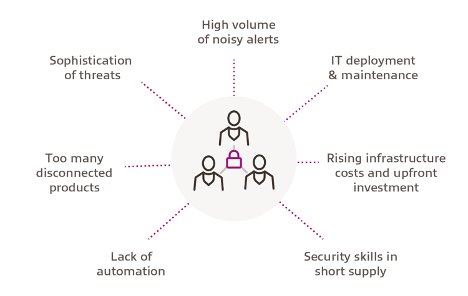
While traditionally, corporate security could get away with predefined prevention and detection mechanisms based on prior knowledge of attack methods, today, separating the wheat from the chaff is difficult. We often observe that admins frequently find themselves handling enormous volumes of events. And, more often than not, data quality is an issue, with false positives frequently leading to triage fatigue.
With the modern era of digitalisation, we now live in an identity-driven security perimeter. Today’s security teams face numerous challenges, including speed and sophistication of threats, and exponential growth of endpoints/assets and associated logs. Corporate security teams are drowning in the volumes of data being generated by digital assets. Data volumes are increasing every day as more operations are digitised and being able to triage quickly is important. The time window to respond when under attack is short; advanced adversaries typically only need hours to gain access, elevate privileges and exfiltrate data.
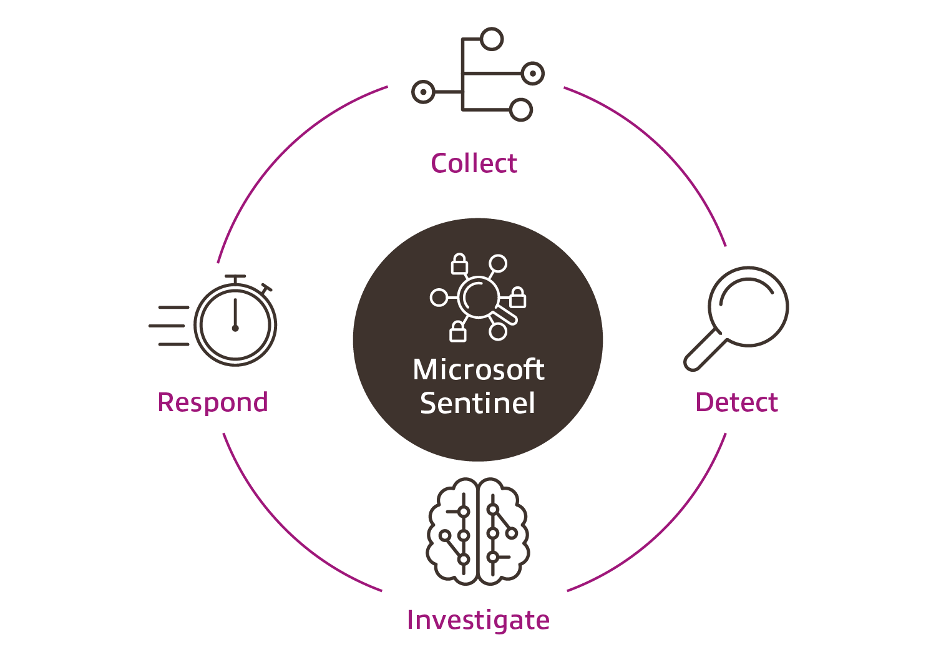
What is Microsoft Sentinel?
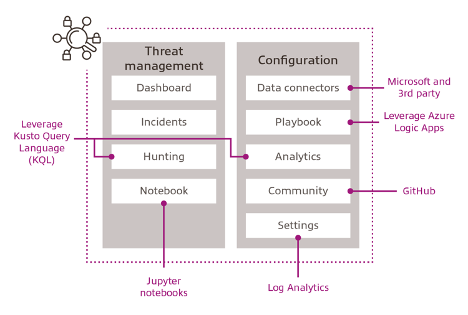
Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) solution built to provide security analysts with a powerful tool to detect and respond to cyberattacks. Sentinel’s SOAR capability is fully customisable and allows security teams to write playbooks that can (if desired) automate the entire response to a security event. For example, once Microsoft Sentinel identifies a malicious domain, a playbook that would automatically add a block rule to the company’s firewalls for that domain can be triggered.