Tech Journal Could You Recover From a Destructive Ransomware Attack?
By Mark Arnold / 25 Oct 2021
By Mark Arnold / 25 Oct 2021

Destructive cyberattacks have become a constant threat in the IT industry. With only a few lines of code stolen, an enterprise may lose a vast amount of confidential data. This type of invasion of privacy impacts businesses, health organizations, local governments and school systems nearly every day — causing disruption to operations and costly recovery actions.
A recent survey of business leaders revealed that 68% observe that their cybersecurity risks are increasing, and 68% lack confidence that they could recover all business-critical data in the event of a cyberattack. While most cyberattacks (71%) are financially motivated, data corruption can stem from different attacks, including insiders.
71%
of breaches are
financially motivated.
$5.2T
of global risk is expected
over the next 5 years.
11 sec.
is the window between
when cyberattacks occur.
While organization will (and should) continue investing in threat prevention and detection solutions, they should also focus on creating effective strategies to respond and recover. Why? Attackers are attacking systems, data and backups. They’re encrypting the backup catalog in addition to the systems and data to render them useless for recovery.
A study by Accenture estimates that the average cost of recovering from a malware attack may reach up to $2.4 million, but it also reports that the cost varies by the organizational size and vertical. Regardless, the cost can be significant. You must consider not only the loss of business and the direct cost to IT, but also the far-reaching damages that will impact the business’s brand and reputation.
Some businesses may be targeted by cybercriminals who request money in exchange for data recovery. While paying the ransom might sound like a good idea to quickly resolve the issue, it comes with many risks and costs. There’s no guarantee that you’ll get the data restored or that the demand won’t increase after making the payment. Moreover, paying a ransom could be an illegal activity in the U.S. and other countries may follow suit.
Simply put, a ransomware attack will cost the organization far more than what’s seen on the surface. The stability of the organization’s revenue and its very existence hinges on the availability of mission-critical data and systems to support the business continuance and recovery operations.
A cyber recovery solution gives organizations a proven and modern strategy to improve the maturity of their security posture. Traditional backup services alone are no longer capable of defending against sophisticated cyberattacks. Many IT analysts and government agencies recommend making backup images or gold copies inaccessible from the network through air-gapped media.
Understanding that a cyber recovery solution is vital in improving your security measures, Dell Technologies designed a solution that will help businesses prevent cyberthreats. PowerProtect Cyber Recovery includes a secure digital vault that’s physically and logically isolated from production and backup networks with an operational air gap. Critical data is protected within a vault in an immutable format with retention periods locked. This enables the best possible chance for recovery if primary backups have been compromised, or the disaster recovery location has been breached or infected.
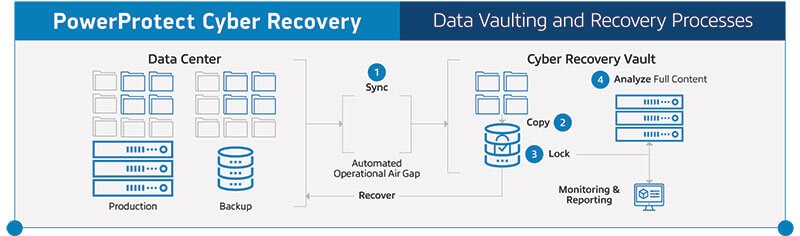
Without a cyber recovery solution, an organization may spend a significant time recovering the last backups without knowing whether the data is secure or compromised. This can be a long, labor intense, iterative and costly process; not exactly what you want when dealing with a business disrupting event.
For this reason, Dell Technologies’ recovery solution constantly monitors data integrity within the vault. If signs of corruption are detected, an alert is generated — conveying the attack vector and the list of files affected. This enables the organization to identify and diagnose potential threats and recover the “known good” data quickly so recovery can occur instantly instead of in weeks or months.
Many organizations delay implementing a cyber recovery solution due to excessive analysis of what data to include in the vault. Dell Technologies recommends starting immediately with your most critical materials. You can expand what data you’re protecting in the vault over time or as budget allows. The chart below outlines some critical materials to consider when getting started.
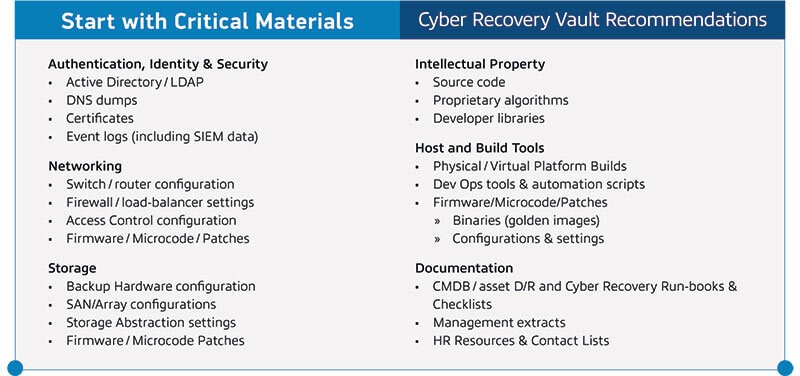
Having a cyber recovery solution partner is your first step in improving the confidentiality and reputation of your business. Keep in mind that protecting your business starts with protecting your data.

Data Protection Channel Lead, Dell Technologies
Mark is a veteran in the IT industry with decades of experience in data platforms. He is an enthusiastic promoter of Data Protection and has held leadership positions in channels, field sales, presales and customer support with time at both the partner and manufacturer sides of the business.